Fun Tips About How To Diagnose Conficker

Because the webpage drags down images of websites that are blocked by the conficker worm (to prevent you from visiting computer security websites, for instance), it can.
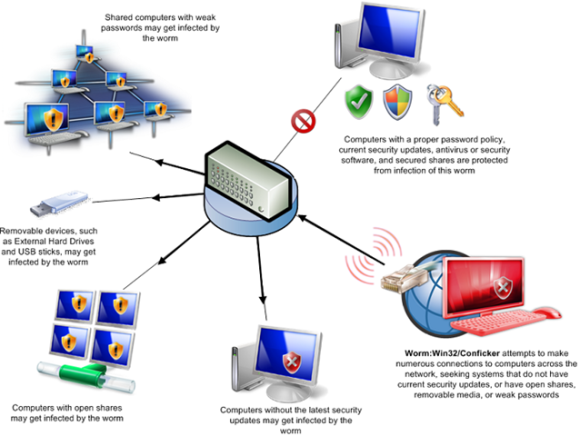
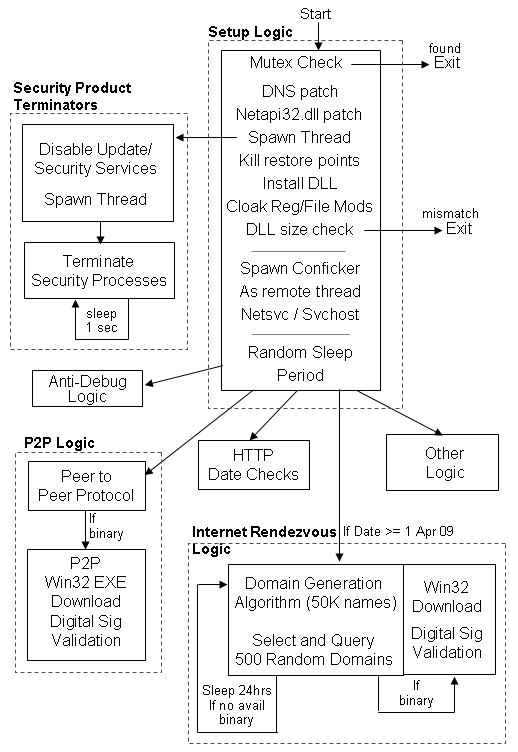
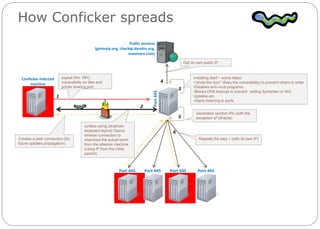
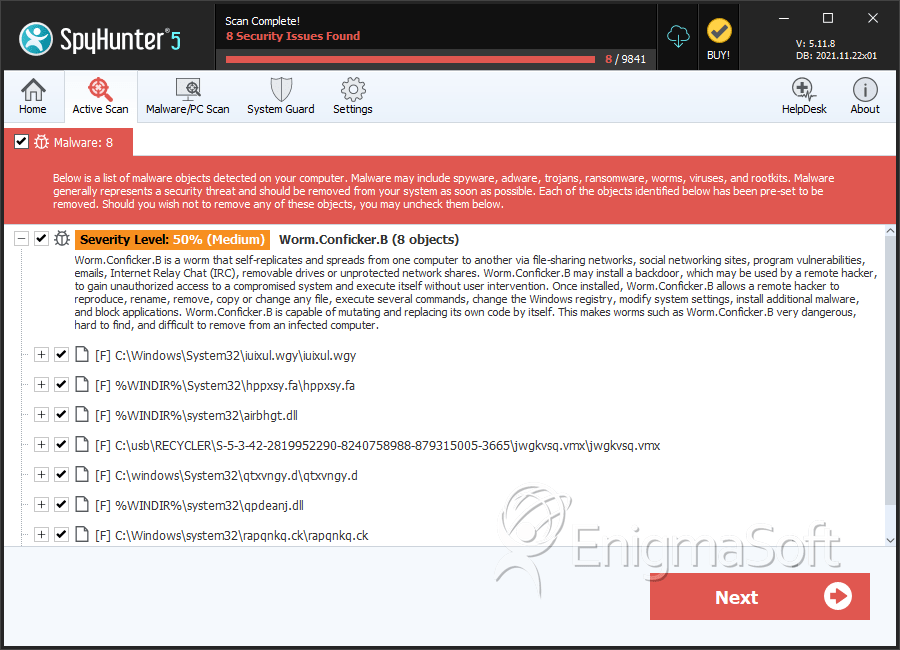
How to diagnose conficker. Conficker has the ability to spread via usb sticks, as well as over a network. The conficker/downadup worm, which first surfaced in 2008, has infected thousands of business networks. Conficker is a computer worm that targets windows, and currently (as of april 21, 2009) infects the largest number of computers worldwide since the sql slammer worm of.
Unpatched computers are most at risk of infection, with conficker exploiting these. Conficker, also known as downup, downadup and kido, is a computer worm targeting the microsoft windows operating system that was first detected in november 2008. Try out opening the antivirus program and also checking the worm:win32/conficker.c discovery log file.
Try to prevent it in the future, however do not fret way too much. As recently as august, whipps cross university hospital nhs trust in east london admitted it had. Panda correctly detects and disinfects conficker.
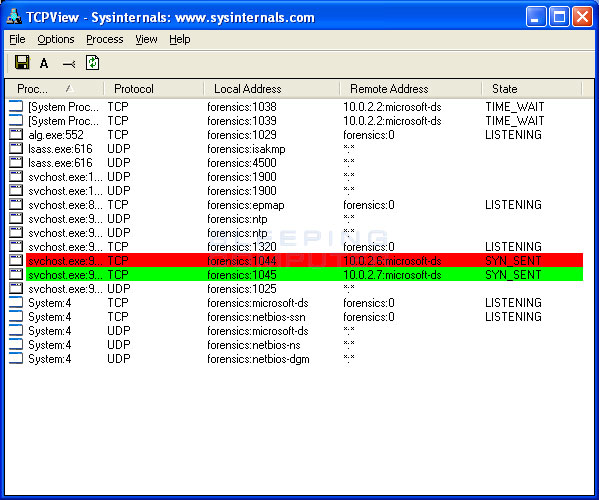
Thomsomc writes joe stewart from the conficker working group has created an eye chart that allows for online identification of conficker b and c infections. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands:
Current versions of conficker will not be allowed to run on a machine that has a working and updated panda antivirus on it. With april 1st come and gone, many people are wondering how do i know if i have the conficker worm? how do you know if you have the conficker virus? Even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying it's not that bad, but trust me.
Within sophos antivirus, clean up the conficker files.